Let’s be honest: online privacy feels more like a myth than a reality these days. You click “accept” on a cookie notice without reading it. You fill out yet another form with your name, birth date, email, and school ID. You share your transcript with an internship provider, unsure who else might see it.
And then you wonder—who really owns your information?
If you’re a student or a university staff member, this question matters more than ever. Every class you attend, every course you complete, every certificate you earn—it’s all tied to your digital footprint. And yet, most of us have little control over how that data is stored, shared, or even sold.
Here’s where verifiable credentials come in.
You can think of them like a modern-day digital lockbox. They’re secure, tamper-proof, easy to share, and—most importantly—under your control. In this blog, we’ll explore what verifiable credentials are, how they work, and why they’re fast becoming the smartest way to protect your privacy online.
What Are Verifiable Credentials, Really?
Let’s break it down.
A credential is just proof. Proof of something about you—like your degree, your age, or your student status.
Now, a verifiable credential? That’s proof you can share digitally, that can’t be faked, and that anyone you share it with can instantly check to make sure it’s real.
Imagine showing someone your driver’s license—but instead of handing it to them, you show a version that only displays the info they need (say, just your age), without revealing your address or license number.
That’s the idea.
It works using cryptography, which locks your data like a secret vault. Only the people you choose can unlock it—and even then, only for what you want them to see.
Here are some real-life examples:
-
A digital student ID stored in your phone
-
A certificate of course completion shared with a job recruiter
-
A verified transcript used to apply for graduate school
And the best part? They’re issued by trusted sources like your university, but you decide when and where to use them.
Why Online Privacy Is a Big Deal (Especially Now)
Let’s not sugarcoat it—online privacy is under threat.
We’re living in a world where personal information is scattered across dozens of platforms, often without our full knowledge or consent. Every time you register for a new app, apply for a service, or submit documents online, bits of your identity are sent out into the digital wild.
And once it’s out there, it’s hard to take it back.
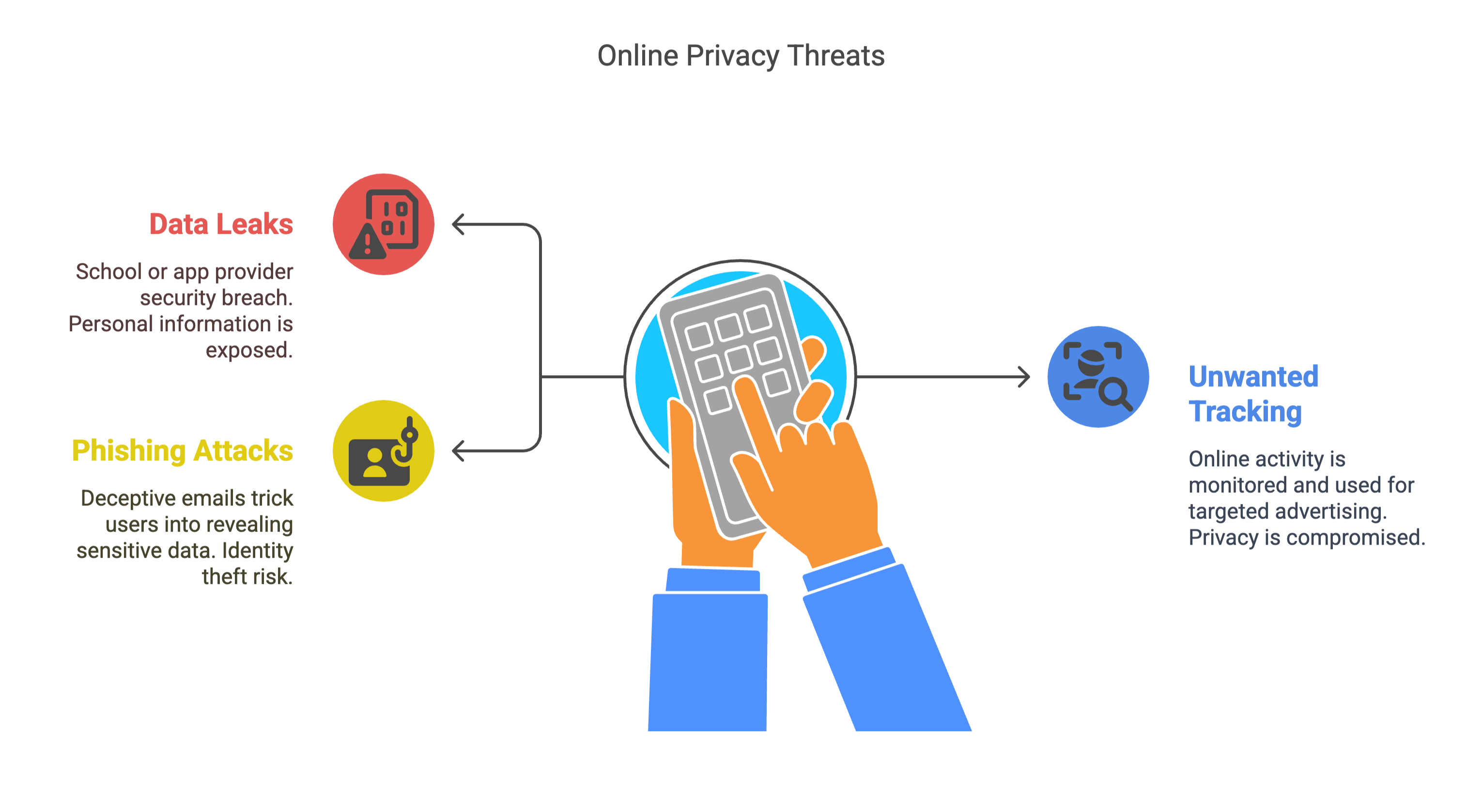
Here are a few pain points you might recognize:
-
Data leaks: Your school or app provider gets hacked.
-
Unwanted tracking: You searched for “best dorm room coffee makers” once—now you’re seeing coffee ads for weeks.
-
Phishing attacks: You get emails pretending to be from your registrar’s office.
Even in university settings, where data protection should be a given, records can be mishandled or exposed. Transcripts sent over email. ID cards lost. PDFs shared and copied without permission.
All of this adds up to a larger problem: You don’t control your data. Others do.
That’s not just frustrating. It’s risky.
How Verifiable Credentials Help Protect Your Privacy
This is where W3C verifiable credentials change the game—quietly, securely, and without asking you to become a cybersecurity expert.
Instead of flooding systems with personal info, verifiable credentials let you show only what’s necessary. Nothing more, nothing less.
Here’s a simple analogy:
Let’s say you’re buying a drink at a college bar. The bartender asks to see your ID. You flash your driver’s license—and suddenly, they know your full name, address, and license number.
Was that really necessary? Probably not.
Now imagine this instead: You show a digital proof that says, “This person is over 21.” That’s it. No address. No ID number. No extra details.
That’s how selective disclosure works. And it’s one of the key strengths of verifiable credentials.
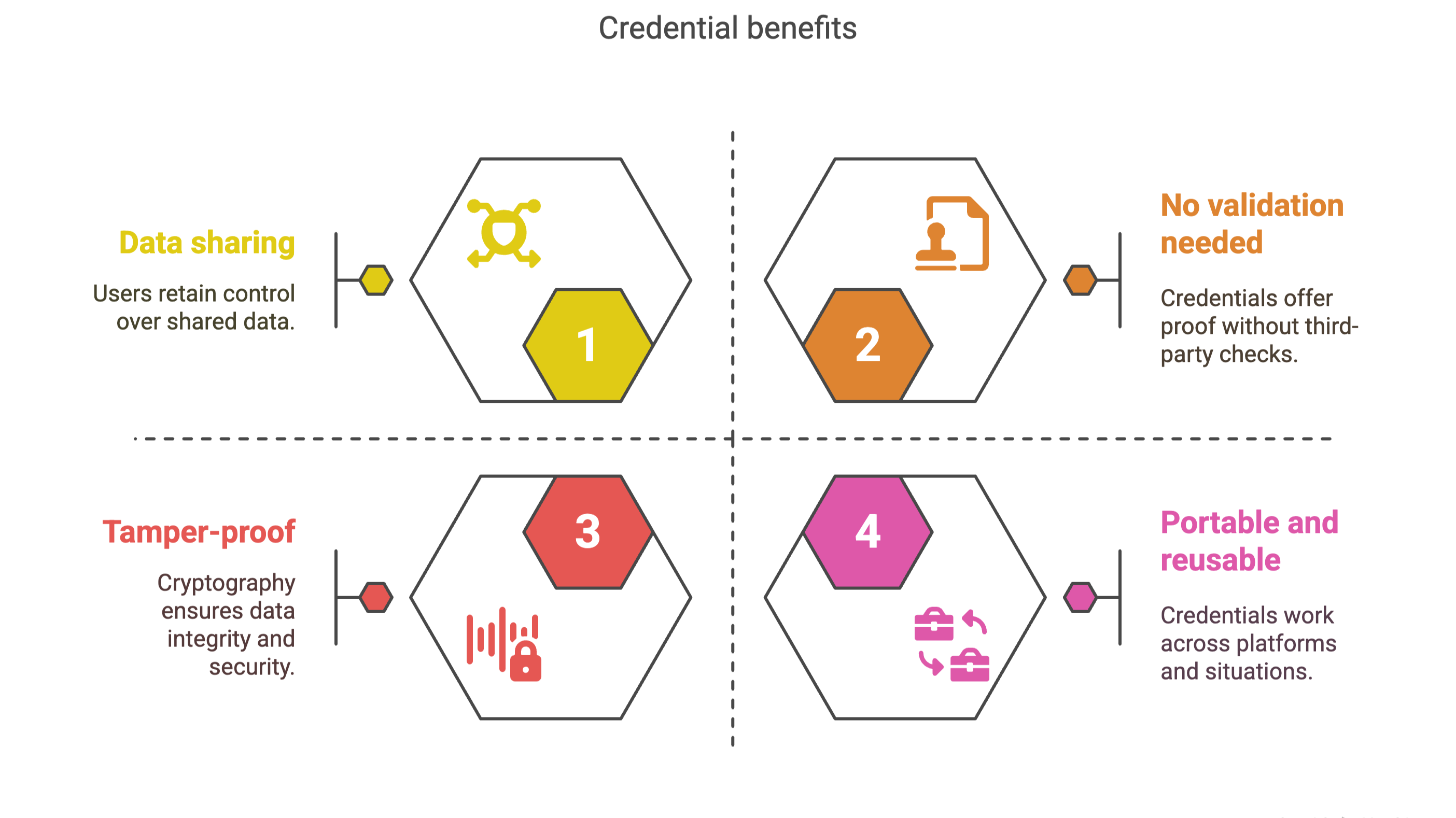
Here’s what they offer:
-
Minimal data sharing – You control what’s shared and with whom
-
No need for third-party validation – The credential itself proves it’s real
-
Tamper-proof protection – Cryptography keeps everything sealed
-
Portable and reusable – Use it across platforms, jobs, and locations
And you don’t have to worry about storing a dozen copies of your transcript or explaining for the tenth time that yes, you graduated last spring.
Real-Life Use Cases on Campus
You might be wondering—how does this play out in real life?
Let’s look at both sides of the campus: the student experience and the admin perspective.
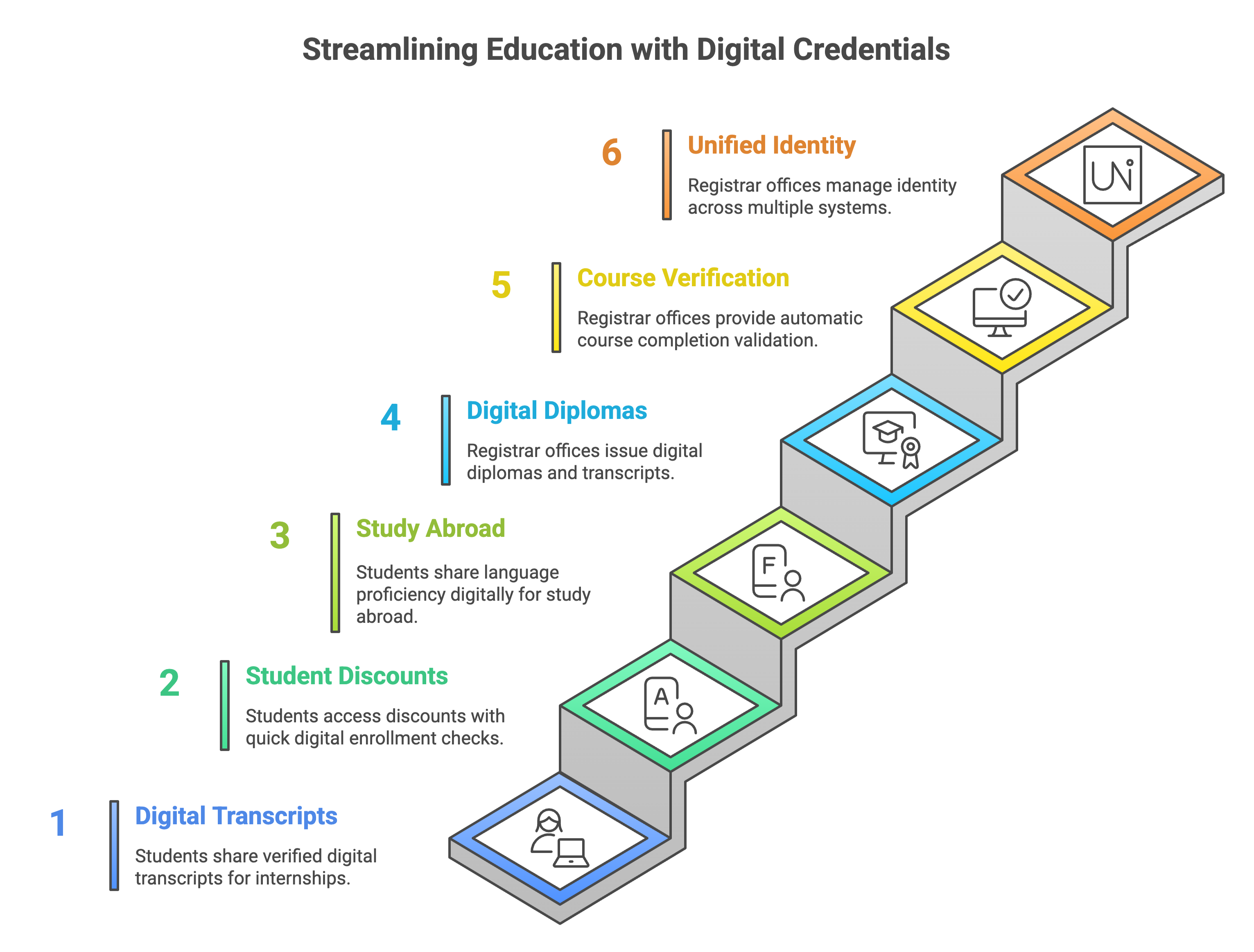
For students:
-
Applying for internships: Instead of uploading clunky PDFs of your transcript, you share a verified digital version.
-
Accessing student discounts: Prove your current enrollment with a quick digital check.
-
Study abroad programs: Share language proficiency or completed prerequisites in seconds.
For registrar offices and staff:
-
Issuing diplomas and transcripts: Reduce printing, mailing, and verification requests.
-
Verifying course completions for job partners: Provide automatic validation without manual follow-ups.
-
Managing identity for multiple systems: Use one secure credential across learning portals, career platforms, and event apps.
Let’s take a real example.
Jamal, a sophomore, is applying for a summer internship in San Diego. The application asks for his transcript, proof of enrollment, and a certificate from a project-based course.
Instead of hunting down three different documents, Jamal logs into his digital wallet. He selects the credentials he wants to share, presses “Send,” and just like that—it’s done.
No printing. No PDFs. No waiting.
The employer gets trusted, verified proof. Jamal keeps control of his information. Everyone wins.
Why Verifiable Credentials Are Better Than Passwords and PDFs
Still thinking, “Why not just stick with what we already use?”
Fair question.
But let’s take a moment to compare.
| Feature | Passwords/PDFs | Verifiable Credentials |
|---|---|---|
| Easy to fake? | Yes | No |
| Share control? | No | Yes |
| Privacy protection? | Weak | Strong |
| Reusable & portable? | Not really | Absolutely |
| Validity verification? | Manual (or none) | Automatic |
Let’s face it—passwords get forgotten, PDFs get lost, and neither tells the full story. When it comes to proving who you are or what you’ve accomplished, traditional methods just don’t hold up anymore—especially in education and employment.
Think about it. Passwords are a one-time access point. They don’t say anything about your identity or your achievements. PDFs, on the other hand, might show that you’ve completed a course or earned a certificate, but they’re easy to fake, hard to verify, and usually end up buried in a download folder. They lack context, security, and shareability.
Now enter verifiable digital records—secure, tamper-proof, and backed by metadata. These aren’t just static files. They’re dynamic proofs that contain:
-
Who issued the credential
-
When and why it was issued
-
What skills or achievements it certifies
-
A digital signature that can be verified instantly
It’s like having a live, self-contained resume that updates when and where you need it. Unlike PDFs, verifiable credentials can’t be altered or reused fraudulently, making them ideal for institutions, students, and employers alike.
Another win? They’re designed for easy sharing and interoperability. Whether you’re adding it to your LinkedIn, submitting it to a job portal, or verifying it through a university’s registrar’s office—verifiable credentials just work. No need to remember passwords, print hard copies, or scan documents. They’re fast, trusted, and made for the modern world.
So, if you’re still relying on old-school methods like login systems or PDF certificates, it might be time to rethink. Verifiable credentials bring trust, ease, and transparency into the mix—and that’s a big deal when every opportunity counts.
Let’s be honest: PDFs are convenient—but once you send one, you lose control over it. Anyone can open it, forward it, even edit it. And passwords? They get stolen all the time.
Verifiable credentials flip this on its head. They’re:
-
Tied to your identity without revealing unnecessary info
-
Impossible to forge, because they come signed by your school or institution
-
Easily revoked if something changes or expires
It’s like handing someone a one-time-use key to a single room—rather than the master key to your whole digital life.
How Universities Can Get Started
If you work in a registrar’s office, you might be wondering, “Sounds good—but how do we make this work in real life?”
The good news is, the groundwork is already there. Many universities are exploring verifiable credentials through:
-
Digital diploma platforms
-
Blockchain-backed identity services
-
Credential wallets that integrate with student portals
Here are a few first steps:
-
Start small – Pilot a program for transcripts or course completions.
-
Use existing partnerships – Many edtech companies now offer integrations.
-
Educate your team – Help staff understand the benefits for both admin and students.
-
Collect feedback – Students will often be your best testers.
There’s no need to switch everything overnight. But taking that first step means you’re giving students more control, while also saving time and resources.
And in the long run? Fewer phone calls. Fewer manual checks. Fewer data breaches.
Challenges and What to Watch Out For
Now, let’s be clear—no solution is perfect.
Many universities are exploring verifiable credentials through solutions like a digital credential management platform:
-
Tech readiness: Older systems may need updates or integration work.
-
User training: Students and staff will need a simple way to learn the new process.
-
Interoperability: Credentials must work across institutions and platforms.
-
Trust: Building confidence in digital records takes time.
It’s not as simple as flipping a switch. But with the right tools and partnerships, it’s absolutely doable. And more importantly? It’s worth it.
Especially when the right systems help you prevent certification and credential frauds before they even begin.
Because at the end of the day, this isn’t just about convenience. It’s about digital dignity—letting people own and protect their identity in a world that too often takes that choice away.
Conclusion: Your Privacy, Back in Your Hands
Let’s return to that question we started with:
Who really owns your information?
With verifiable credentials, the answer can finally be: You do.
You decide what to share. You decide who sees it. You decide when and how to use it.
In a world where privacy often feels like a thing of the past, verifiable credentials offer something rare: a chance to rebuild trust—one verified click at a time.
So whether you’re a student applying for your first job, or a registrar looking to streamline services, remember this:
You don’t need more passwords or PDFs.
You just need better tools.
And now, you have them.
Let’s circle back—who holds the keys to your personal data? With verifiable credentials, you finally do. You control what gets shared, who gets to see it, and for how long. In a world where over-sharing is the norm, that kind of control isn’t just useful—it’s necessary.
Whether you’re a student applying for an internship or part of a registrar’s office trying to simplify workflows, the benefits are clear. Less back-and-forth, fewer security risks, and more peace of mind. It’s like handing over just the right puzzle piece, without showing the whole picture. And once you’ve tried it, going back to PDFs and passwords will feel like rewinding a VHS tape in a world of streaming.
If you’re curious how this works in practice, check out CertifyMe. It helps schools and students issue and manage verifiable credentials in a way that’s secure, easy, and built for today’s digital needs.
Whether you’re looking to protect student records or speed up verification tasks, this platform has you covered. Want to see how it fits your needs?
Book a demo call and take the first step toward smarter, safer credentialing.

 Author :
Author :